Even though two-factor authentication isn’t the silver bullet many make it out to be, I’m still a big fan of it and think that it should be offered by any web service that wants to be taken seriously. It’s completely pointless, though, if the service doesn’t also have strong account recovery policies, or if their customer support staff doesn’t enforce them.
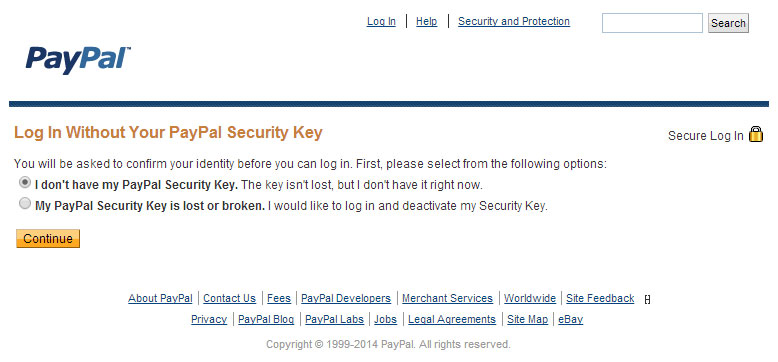
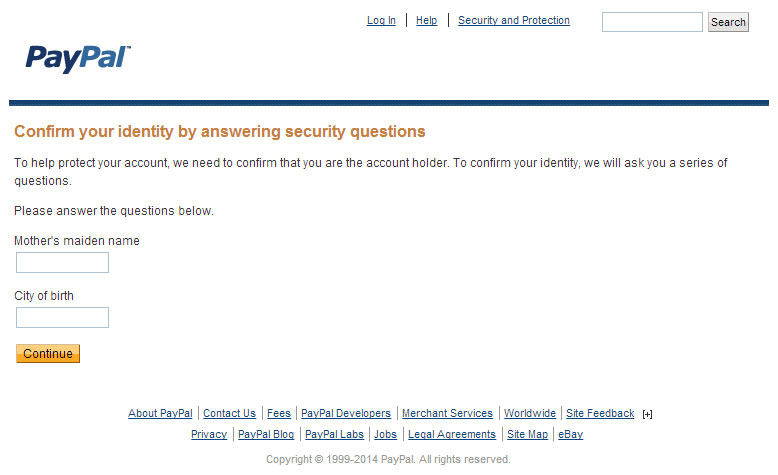
PayPal is a great example of this. When you login with your username and password, you’re prompted for your one-time password, but you’re also given an easy and convenient way to bypass the entire process by entering your mother’s maiden name and your city of birth — both of which are trivial for attackers to obtain from public records or social engineering.
By offering this to attackers, they’ve basically neutered their two-factor authentication implementation to the point where it’s really nothing more than security theater. As a workaround, users can generate random passwords and enter those as answers to the security questions, rather than using the true answers.
A better way to do it would be to require that users generate a set of backup one-time passwords that they can use to login if they lose their hardware token. They should be required to enter one of them during the setup process, to ensure that they actually have them, and they should be instructed to keep them in a secure location, like a home safe of safe-deposit box. If they don’t have a backup code, then they aren’t given access to the account. Period. No exceptions.
If the service has a justifiable use case to allow recovery without a backup password, then the person making the request should be required to provide multiple factors of proof of their identity; for example, their social security number and a photocopy of their driver’s license. Those would have to be obtained during account setup, though, so that their authenticity could be verified during the recovery process.
In either case, any attempt to bypass two-factor auth or use a backup code should trigger an automated alert to both the e-mail address and phone number on file, to alert the owner of a possible unauthorized recovery attempt. If access will be granted by support staff, it should be delayed by 10 days to give the legitimate owner a chance to deny the request.
For the policies to be effective, support staff have to be properly trained and motivated, which seems unlikely if they paid minimum wage and work in conditions that would make anybody hate their job. All account recovery tickets should be handled by a small group of veteran techs who are trained against social engineering, and who strictly enforce the recovery policies.
3 Risks and Downsides to Two-Factor Authentication | Trick5 Simplify The Technology
3 Risks and Downsides to Two-Factor Authentication | MINDSCULPT.ME
3 Risks and Downsides to Two-Factor Authentication - Guides Geek
3 Risques et inconvénients de l'authentification à deux facteurs | Moyens I/O